  |
|
|
Customer Support | Products | Company Info | Links | Helpdesk |
|
|
||||
| Home | |
| Products | |
| Reviews | |
| Demonstration | |
| Testimonials | |
| Photos | |
| Specifications | |
| FAQ | |
| Press releases | |
| Download | |
| Legal Disclaimer | |
| Affiliates | |
| Distributors | |
|
|
Interface Security KeyGhost II Professional
Written
By: Altonzo
Date submitted:
21 December, 2000
Type of Article: Product Review
Language English, Romanian
Independent Review:

Final Mark: 23/25
Introduction
![]()
Looking
at this title I doubt that you can tell me what I'll review in this article.
First I want to tell you that it was hard to review this device. Why?
Simply because it's not easy to talk about something with no known predecessors
and no competitors. Supposing that company X introduces today a PC running
10 times faster than a 1Ghz Thunderbird do you think that someone would
have the gouts to say: it's not overclockable? No, or he must be crazy.
I was in front of the egg. Maybe this is not the first device of this
kind but it's the first available to the public. Well, I think that I've
succeeded to make you curious, let's see what's about.
First look It has been proved that it's possible to make software able of intercepting key presses. In the beginning these programs were created by hackers that observed their potential: an easy way to gain root access. And it worked. Today it's impossible to gain a higher access using this method because there are no operating systems which allow program loads prior to authentification process. Remember that in order to login in WinNT/2000 you have to press ctrl-alt-del. It's possible to intercept password if the user use a Telnet to login to a remote computer even if this connection is encrypted. Until now I haven't see a hardware product capable of intercepting key presses. KeyGhost is a device that connects between your keyboard and PC, able to store keystrokes. It is produced by a company located in New Zealand called Interface Security. They have a full range of KeyGhost devices, the differences being capacity, encryption and physical form. Take a look to the below table.
| Model |
Capacity
|
Ghost
Playback
|
Encryption
|
Compatible
with Turbo Download Adapter
|
Casing
/ Wh
|
| Keyghost Professional SE | 2,000,000 Keystrokes |
Yes
|
128
bit
|
Yes
|
EMC
Balun
style |
| Keyghost Professional | 1,000,000 Keystrokes |
Yes
|
128
bit
|
Yes
|
EMC
Balun
style |
| Keyghost Standard | 500,000 Keystrokes |
Yes
|
Basic
|
No
|
EMC
Balun
style |
| Keyghost Home Edition | 128,000 Keystrokes |
Yes
|
None
|
No
|
EMC
Balun
style |
| Keyghost Security Keyboard (Pro SE) | 2,000,000 Keystrokes |
Yes
|
128
bit
|
Yes
|
Inside
Keyboard |
| Keyghost Security Keyboard (Pro) | 1,000,000 Keystrokes |
Yes
|
128
bit
|
Yes
|
Inside
Keyboard |
| Keyghost Security Keyboard (Standard) | 500,000 Keystrokes |
Yes
|
Basic
|
No
|
Inside
Keyboard |
As you can see there are seven models, the most advanced being able to memorize over 2,000,000 keystrokes. A full A4 page has about 3,000 characters ( including spaces ) meaning that the top model is able to store about 600 pages! Sincerely speaking I doubt that someone will ever buy it to store keystrokes. There are devices far more advanced that can hold the information. I do not exclude certain areas where a Keyghost can be a dream but it's less common. To understand better what I want to say take a look to the picture representation of the Keyghost Professional.
![]()
Keyghost Professional At a first, second and even final look it seems to be some kind of adapter. A person with brain could ask "What the hell does it do?". After all it doesn't covert anything, it looks more like a filtering device, very common for data caring cables ( look at your monitor cable ). Anyway to start thinking about it you have to observe it first. To tell you the truth if someone would ever install a Keyghost on our server the root access is just a matter of patience :).
Installation
There is no person in this world able to use a computer that is not capable of installing Keyghost in less than one minute. Keyghost is shipped in a box that contains several installation tips and two adapters from/into AT keyboard to PS/2. So older computers are also supported. Let's go to software installation. Funny to say, but Keyghost requires no software. It works on any PC with any OS. Cool, but how can this be done?
How it works?
Keyghost is not a dump memory writer, it is able to interpret incoming key presses and encrypt them. To further detail this process take an example: the string "abcdef". If set by user as password, KeyGhost display a little menu in any text editor.
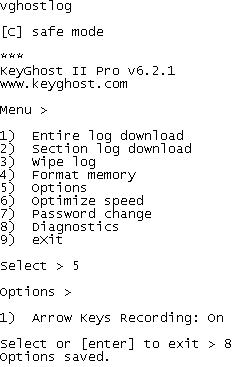
You can change the password, view the options, wipe log, display log, etc. The drawback is that you can view logs at the speed of the keyboard interface. As you can see in the above caption I have introduced "vghostlog" the default password of the Keyghost and the menu showed up. I tried "5" to show options and Keyghost promptly displayed them. Now take a look below to a fragment of the log, displayed by "1".
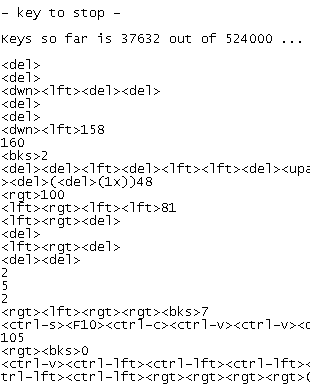
Keyghost recognizes all the keys, even combinations and displays them in an easy form. The log fragment is an example of Windows navigation. Do not try to understand it. The device is also able to detect power-on and plug-ins for which generates a <pwr> or a <on>.
Conclusion
I liked this device. Small and effective this could be a nice toy for James Bond. Take care that the manufacturer didn't recommend the use of Keyghost for hacking propose :). I liked that you don't need specific software to view or change the device options and that it is very resistant to shock. Supposing that someone finds the Keyghost, cuts the plastic and remove the memory chip; it's almost impossible to break into it. The 128-bit encryption, if powered by a decent implementation makes decryption impossible. If you ask me how reliable this thing is the answer is very because it uses flash memory for storage which theoretically lasts for a very long time! The easiest way is to brute force attack it which is easy but as inefficient as the previous method if the user use a long password. The price may represent a problem, but if you really need it I bet that this are clever spend money.

Final
Mark: 23/25
Check out more reviews >>
