  |
|
|
Customer Support | Products | Company Info | Links | Helpdesk |
|
|
||||
| Home | |
| Products | |
| Reviews | |
| Demonstration | |
| Testimonials | |
| Photos | |
| Specifications | |
| FAQ | |
| Press releases | |
| Download | |
| Legal Disclaimer | |
| Affiliates | |
| Distributors | |
|
|
Interface Security Keyghost II Std
Written
By: Mukundh Pandian
Date submitted: 1 August 2000
Type of Article: Product Review
Independent Review:

Introduction
When I first heard about the KeyGhost I immediately conjured up images of CIA operatives breaking into foreign leaders offices in order to install this adapter on their keyboard and thus monitoring everything that was typed. After testing the KeyGhost and using it for a week I now realize that it has much more practical purposes that we can all benefit from.
The KeyGhost is a piece of hardware that once hooked up to your keyboard will record every keystroke no matter what OS you are using.
The company is also selling keyboards with a KeyGhost built inside the keyboard so that it cannot be seen. Currently the KeyGhost uses a PS2 connector but a USB version of the KeyGhost is under development.
The KeyGhost is very small and looks like an adapter of some sort.
![]()
There are several versions of the KeyGhost that vary according to capacity, encryption, and inclusion of a fast download adapter. Here is a nice table that sums up the different models:
| Model |
Capacity
|
Ghost
Playback
|
Encryption
|
Compatible
with Turbo Download Adapter
|
Casing
/ Wh
|
| Keyghost Professional SE | 2,000,000 Keystrokes |
Yes
|
128
bit
|
Yes
|
EMC
Balun
style |
| Keyghost Professional | 1,000,000 Keystrokes |
Yes
|
128
bit
|
Yes
|
EMC
Balun
style |
| Keyghost Standard | 500,000 Keystrokes |
Yes
|
Basic
|
No
|
EMC
Balun
style |
| Keyghost Home Edition | 128,000 Keystrokes |
Yes
|
None
|
No
|
EMC
Balun
style |
| Keyghost Security Keyboard (Pro SE) | 2,000,000 Keystrokes |
Yes
|
128
bit
|
Yes
|
Inside
Keyboard |
| Keyghost Security Keyboard (Pro) | 1,000,000 Keystrokes |
Yes
|
128
bit
|
Yes
|
Inside
Keyboard |
| Keyghost Security Keyboard (Standard) | 500,000 Keystrokes |
Yes
|
Basic
|
No
|
Inside
Keyboard |
Now you are probably saying ok so the KeyGhost can record every keystroke but how do I view that information? To view the information it collects you use a menu system that can be accessed from any word processor or text box. I tried it in several places such as the URL bar in Internet explorer and in Half-Life's console and it worked in both. To access this menu you type your eight to twelve letter password and a menu will popup. Here is a screenshot of the menu:
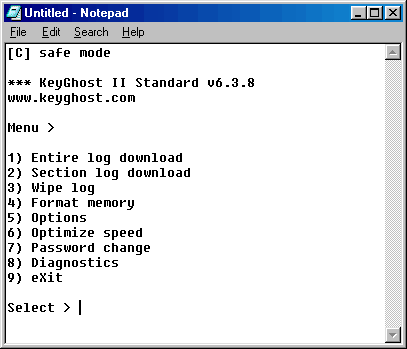
From this menu you can download the entire log, parts of the log, erase the log, change your password, and a few other neat things. It takes about 25 minutes to download a full log but with the fast download adapter it only takes a few seconds.
The KeyGhost has a number of uses. Being a college student I am often writing papers or a news updates for my website when good old Windows crashes on me. Using the KeyGhost I loose nothing and I am able to completely recover whatever I was working on. The KeyGhost would also benefit coders and anyone who uses their computer for important information. I had a friend who worked for four hours on a C program last semester only to have his computer crash. He hadn't saved any of his work and he had to redo the entire program. The KeyGhost could also be used to monitor employees in order to make sure they are not giving away company secrets. As you can see there are a number of uses for the KeyGhost.
I broke into Sadam's palace twice to install the KeyGhost but unfortunately I did not learn anything useful. Sadam Hussein just visits Slash Dot a few times each day and not much else.
Overall
this is a very useful product that can save you time and money.
Check out more reviews >>
